What is a firewall in cybersecurity, and why does it still matter in a cloud-first world?
A firewall is no longer just a perimeter defense blocking unauthorized traffic. In modern enterprise environments, it acts as a multi-layered control system that protects infrastructure, applications, endpoints, and data flows.
As organizations migrate to cloud enviroments, adopt microservices, and operate distributed teams, the firewall evolves from a static network barrier into an adaptive security architecture.
For today’s technology leaders, firewall architecture is a core architectural choice that directly impacts risk exposure, scalability, compliance, and operational resilience.
The strategic stack of the modern firewall
A modern firewall is a coordinated system of security controls operating across multiple levels of enterprise architecture.
From cloud infrastructure to application logic to human behavior, each layer contributes to a defense-in-depth model designed to minimize attack surfaces, detect anomalies early, and reduce lateral movement.
To make this architecture actionable, we organize modern firewall design into four interconnected strategic domains:
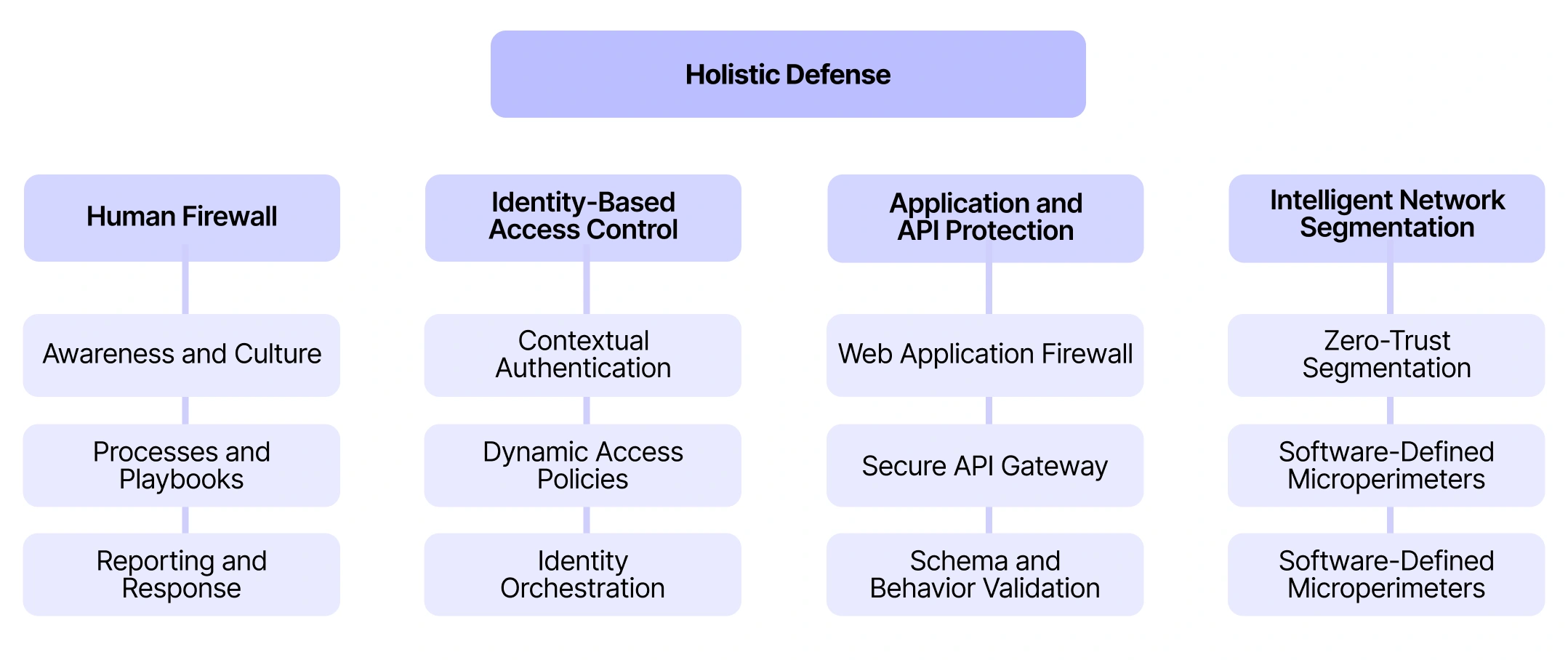
Each domain plays a distinct role. Their effectiveness, however, depends on orchestration, not isolation. That’s why modern firewall architecture is built in layers, from infrastructure controls to human awareness.
This layered model ensures security is integrated into the architecture itself, enabling true defense in depth without blind spots. One of the most critical layers in this model operates at the application level, where business logic, APIs, and customer-facing services are exposed. This is where the Web Application Firewall (WAF) becomes essential.
How does a Web Application Firewall work?
Most enterprise attacks target applications and APIs, so a Web Application Firewall (WAF) protects the business layer by inspecting HTTP and HTTPS traffic, blocking malicious requests, preventing injection attacks, and enforcing security rules aligned with application logic.
In practical terms, a WAF helps protect: web applications, APIs, authentication flows, and transaction endpoints.
At Devlane, we configure these policies based on application behavior, risk exposure, and traffic patterns, ensuring protection adapts as the architecture evolves.
However, application-layer protection alone is not enough. Firewall architecture must extend beyond HTTP traffic and into the cloud infrastructure itself, where network exposure, permissions, and segmentation define the real attack surface.
1. Security groups: Foundational network control
Security Groups (SGs) act as stateful virtual firewalls for AWS EC2 instances. They define which traffic is allowed to enter or leave a workload. Unlike traditional firewalls, SGs operate under an implicit deny model and only support explicit allow rules, reinforcing a restrictive security posture by default.
When properly designed following the principle of least privilege, Security Groups significantly reduce unnecessary exposure at the infrastructure level.
2. AWS GuardDuty: Continuous threat detection
While Security Groups prevent unauthorized access, GuardDuty focuses on detection.
GuardDuty continuously monitors AWS environments for suspicious API calls, anomalous behavior, malicious IP communication, and compromised credentials.
The combination of prevention (ECS Security Groups), security alerts (managed by AWS Cloudwatch), detection (GuardDuty) and automated response mechanisms create a robust defense-in-depth model for cloud infrastructure.
Implemented correctly, this architecture reduces risk while preserving operational agility. However, infrastructure-level controls are not sufficient on their own.
3. Server-level Firewalls
Server firewalls add an additional containment layer directly at the workload level. The best practice is to implement highly restrictive policies, allowing communication only for explicitly required services and ports.
At Devlane, we implement server-level policies aligned with:
- Application architecture
- Service dependencies
- Zero-trust segmentation principles
This approach ensures that even if a breach occurs, lateral movement is limited and impact is contained. In addition, we continuously monitor cloud server activity through our Security Information and Event Management (SIEM) platform, enabling real-time anomaly detection and faster incident response.
4. Endpoint Firewalls
Endpoint-level protection adds another critical control layer within modern firewall architecture. Through our Extended Detection and Response (XDR) platform, we monitor and control endpoint activity across devices, servers, and workloads.
By applying firewall rules directly at the endpoint level, we reduce the risk of unauthorized communication, lateral movement, and exploitation of compromised devices.
This ensures that protection is not limited to the network or cloud perimeter, but enforced at the workload itself.
The strategic core: The human firewall
The most advanced security tools won’t help if the human layer fails. A human firewall in cybersecurity turns the weakest link into the first line of defense.
Most incidents today involve phishing, credential misuse, or delayed reporting. That is why the Human Firewall is not a training initiative. It is a structured security function.
A Human Firewall turns employees into active participants in defense, integrating culture, governance, and enabling technology into a single operational layer.
At Devlane, this is a continuous practice. Security leadership ensures that information protection is actively safeguarded, while managers and technical teams share responsibility for operational resilience.
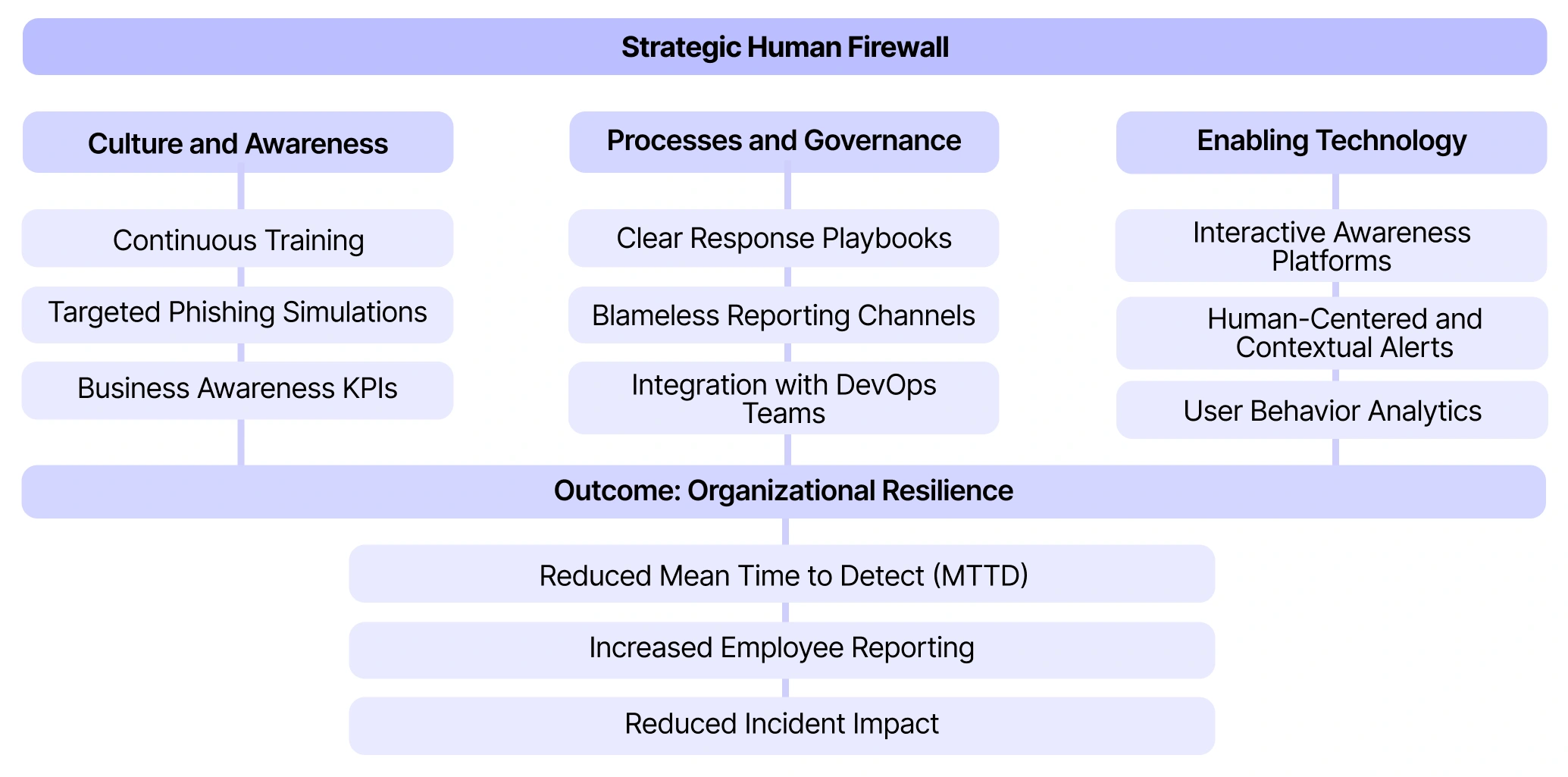
The Strategic Human Firewall operates across three coordinated dimensions.
- Culture and awareness: Continuous training, targeted simulations, and measurable security KPIs ensure that awareness translates into behavior.
Some technical awareness strategies we use at Devlane:
- Segmentation by risk profile: We implement classification systems that categorize users based on threat exposure, critical functions, and historical patterns.
- Omnichannel integration: Awareness is embedded directly into day-to-day work through: onboarding training in cybersecurity awareness, communications through instant messaging channels, training through our cybersecurity-oriented platform, Ad-hoc meetings to address gaps and real-time alerts on software behavior at each endpoint.
- Processes and governance: Clear response playbooks, blameless reporting channels, and integration with DevOps teams make security operational rather than reactive.
- Enabling technology: Interactive awareness platforms, contextual alerts, and user behavior analytics reinforce human decision-making in real time.
Role-Based technical training program
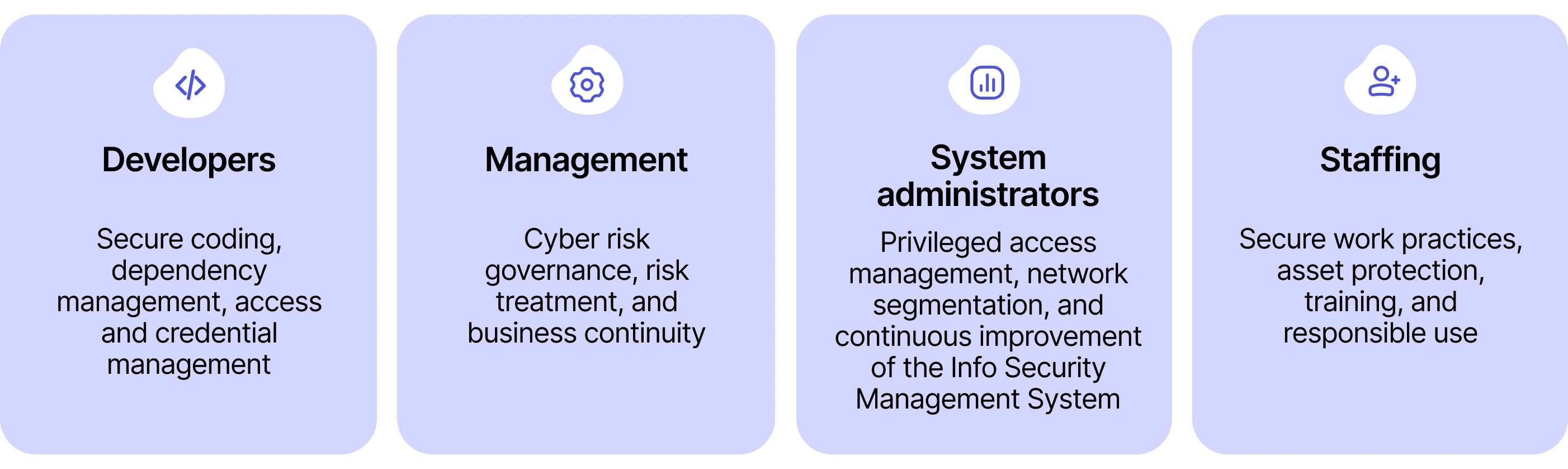
Security maturity cannot rely on generic training. Different roles face different risk exposures. Developers, managers, infrastructure engineers, and operational staff interact with systems in fundamentally different ways, and their security enablement must reflect that reality.
At Devlane, we design role-based technical training programs aligned with organizational function and access level. This structured capability matrix ensures that each team member understands not only core security principles, but also the specific risks associated with their responsibilities.
By aligning training with operational reality, we reduce preventable vulnerabilities before they materialize in production environments.
Gamification with measurable purpose
Awareness only creates value when behavior becomes measurable. We translate security behaviors into visible operational metrics through dashboards, evaluation systems, and structured risk scoring. This allows organizations to track maturity over time rather than relying on theoretical completion rates.
To reinforce real-world preparedness, we implement advanced phishing simulations with varying levels of sophistication, as well as incident-response exercises that replicate realistic breach scenarios. These simulations help teams develop reflexes.
Security as an ongoing commitment
Security awareness is a system. Our model operates as a closed-loop framework in which performance data continuously informs improvement.
We analyze behavioral metrics to refine training programs, adjust simulation complexity based on observed results, and update content in response to emerging threats. When persistent gaps are identified, additional technical controls or policy adjustments are introduced. When processes create unnecessary friction, they are simplified.
This dynamic tuning ensures that security evolves alongside the organization. We also incorporate micro-learning, adaptive training platforms, and new simulation formats that personalize learning paths according to user behavior and exposure levels.
Closing: Security as a system and a growth enabler
Modern firewall architecture demonstrates that effective security is an integrated system where technological controls and human awareness reinforce each other.
For growing companies, this distinction is critical. As engineering teams scale, cloud environments expand, and client expectations increase, the human layer often becomes the most underestimated risk surface. A structured Human Firewall reduces preventable incidents, shortens detection times, strengthens reporting culture, and limits operational impact when incidents occur.
This directly protects intellectual property, client data and trust, compliance posture, and business continuity.
Security, in this context, is not a cost center. It is an operational stabilizer and a growth enabler. At Devlane, we design and operate this model as a structural component of enterprise growth.
If you are scaling your tech organization and security is a strategic priority, let’s connect and explore how we can support your growth with enterprise-grade standards built in from the start.

Other Blog Posts

Firewall Architecture for the Modern Enterprise

AI in Healthcare: The Technologies Redefining Care Delivery Today





